Aimbridge Connection
Connecting You to the Latest in Hospitality and Travel Insights.
Data Transfer: Adventures in the Digital Wilderness
Embark on thrilling journeys through the digital wilderness! Discover tips and tales of data transfer that will transform your tech adventures.
Understanding Data Transfer Protocols: A Guide to the Digital Wilderness
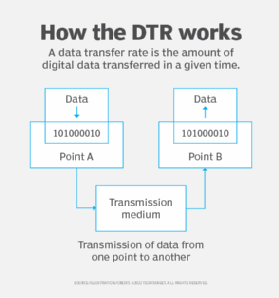
In the ever-evolving world of technology, data transfer protocols serve as the backbone of digital communication. These protocols dictate how data is transmitted across networks, ensuring that information is sent and received accurately and efficiently. Some of the most common protocols include HTTP for web traffic, FTP for file transfer, and SMTP for email communication. Understanding these protocols is essential for anyone looking to navigate the digital wilderness, as they play a crucial role in facilitating connectivity between devices and applications.
When diving deeper into data transfer protocols, it’s important to recognize the various layers and standards that govern them. For example, the OSI model outlines seven layers of networking, with data transfer protocols primarily operating at the transport and application layers. Additionally, each protocol comes with its unique set of functionalities and security measures, which can significantly impact how efficiently data travels across the internet. Whether you are a developer, network engineer, or simply an enthusiast, familiarizing yourself with these concepts will enhance your ability to leverage the full potential of digital communication.
If you're looking to expand your connectivity options, exploring the Top 10 Powered USB Hubs can be a great start. These hubs provide additional power to support multiple devices simultaneously, ensuring efficient data transfer and charging. From compact designs to multi-port options, there's a powered USB hub to suit every need.
Common Pitfalls in Data Transfer: Navigating the Obstacles
Data transfer is a crucial process in today's digital landscape, but several common pitfalls can hinder its efficiency and reliability. One major obstacle is the lack of proper planning. Without a well-defined strategy, organizations may overlook essential details such as bandwidth limitations, data integrity checks, and compliance requirements. To avoid this, it is vital to conduct a thorough assessment of all data transfer needs before initiating the process. As a best practice, consider implementing a checklist that addresses all key factors to ensure a seamless transfer.
Another significant challenge arises from inadequate security measures during the data transfer process. Transferring sensitive information over unencrypted channels can lead to data breaches and unauthorized access, compromising both privacy and trust. Organizations should prioritize the use of robust encryption methods and secure transfer protocols to protect their data. Additionally, training staff on the importance of security practices can foster a culture of awareness, reducing the likelihood of human error. By addressing these common pitfalls, companies can navigate the obstacles associated with data transfer more effectively.
How to Ensure Secure Data Transfer: Tips for Adventurers
For adventurers who rely on digital devices while exploring the great outdoors, ensuring secure data transfer is crucial. Whether you are sharing images from your latest trek, saving vital travel information, or updating your blog in real-time, using a secure connection can prevent sensitive data from falling into the wrong hands. Here are some essential tips to keep in mind:
- Use a Virtual Private Network (VPN): A VPN encrypts your internet connection, safeguarding your data from potential threats, especially when using public Wi-Fi networks.
- Enable Two-Factor Authentication: This adds an extra layer of security to your accounts, making it harder for unauthorized users to access your data.
Additionally, always be cautious when sharing information on social media or public forums during your adventures. Remember to:
- Limit your data sharing: Avoid sharing real-time locations or sensitive information that could compromise your safety.
- Use encryption tools: Utilize software that encrypts files and messages, ensuring your data remains private during transfer.
By following these practices, you can enjoy your adventures while maintaining the security of your digital assets.